Page 40 - CPTE_Lab_Guide_Sample
P. 40
Official Student Lab Guide
Lab 4 – Detecting Live Systems
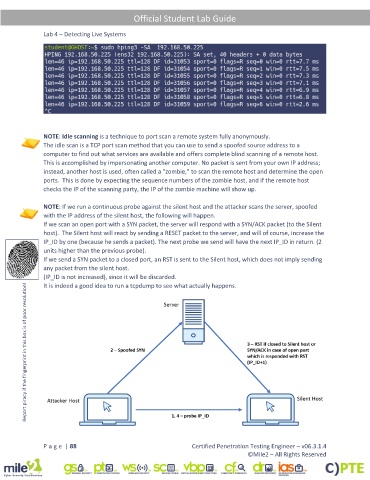
NOTE: Idle scanning is a technique to port scan a remote system fully anonymously.
The idle scan is a TCP port scan method that you can use to send a spoofed source address to a
computer to find out what services are available and offers complete blind scanning of a remote host.
This is accomplished by impersonating another computer. No packet is sent from your own IP address;
instead, another host is used, often called a "zombie,” to scan the remote host and determine the open
ports. This is done by expecting the sequence numbers of the zombie host, and if the remote host
checks the IP of the scanning party, the IP of the zombie machine will show up.
NOTE: If we run a continuous probe against the silent host and the attacker scans the server, spoofed
with the IP address of the silent host, the following will happen.
If we scan an open port with a SYN packet, the server will respond with a SYN/ACK packet (to the Silent
host). The Silent host will react by sending a RESET packet to the server, and will of course, increase the
IP_ID by one (because he sends a packet). The next probe we send will have the next IP_ID in return. (2
units higher than the previous probe).
If we send a SYN packet to a closed port, an RST is sent to the Silent host, which does not imply sending
any packet from the silent host.
(IP_ID is not increased), since it will be discarded.
Report piracy if the fingerprint in this box is of poor resolution!
It is indeed a good idea to run a tcpdump to see what actually happens.
P a g e | 88 Certified Penetration Testing Engineer – v06.3.1.4
©Mile2 – All Rights Reserved