Page 22 - CPTE_Lab_Guide_Sample
P. 22
Official Student Lab Guide
Lab 4 – Detecting Live Systems
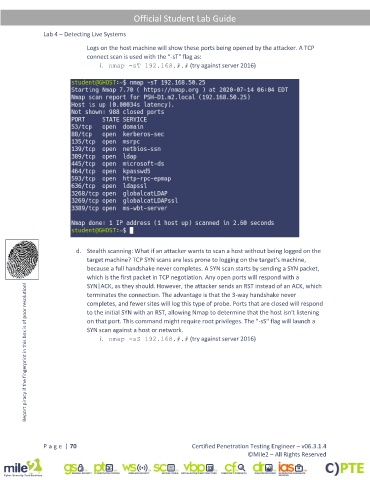
Logs on the host machine will show these ports being opened by the attacker. A TCP
connect scan is used with the "-sT" flag as:
i. nmap -sT 192.168.#.# (try against server 2016)
d. Stealth scanning: What if an attacker wants to scan a host without being logged on the
target machine? TCP SYN scans are less prone to logging on the target's machine,
because a full handshake never completes. A SYN scan starts by sending a SYN packet,
which is the first packet in TCP negotiation. Any open ports will respond with a
Report piracy if the fingerprint in this box is of poor resolution!
SYN|ACK, as they should. However, the attacker sends an RST instead of an ACK, which
terminates the connection. The advantage is that the 3-way handshake never
completes, and fewer sites will log this type of probe. Ports that are closed will respond
to the initial SYN with an RST, allowing Nmap to determine that the host isn't listening
on that port. This command might require root privileges. The "-sS" flag will launch a
SYN scan against a host or network.
i. nmap -sS 192.168.#.# (try against server 2016)
P a g e | 70 Certified Penetration Testing Engineer – v06.3.1.4
©Mile2 – All Rights Reserved